Firewalls: General Concepts and Principles
In the IT domain, a firewall is a hardware/software system that isolates an organization's internal network from the Internet, allowing some packets to pass while blocking others. The most classic analogy used to explain firewalls, and which effectively summarizes their functioning, is that of a fire wall. Just as a fire wall prevents a fire from spreading, a firewall prevents potential cyber threats from spreading within the network.
How Firewalls Work
A firewall allows a network administrator to control communications between the outside world and resources within the managed network, managing all incoming and outgoing traffic. One possible firewall placement is: The one highlighted in the figure below.
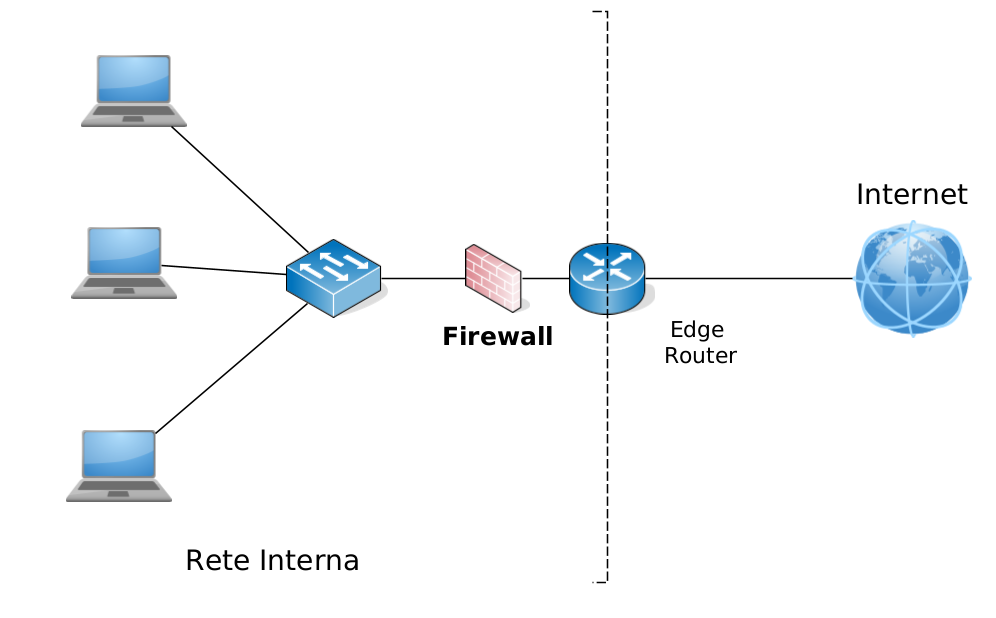
A firewall obeys three principles:
- All traffic from outside to inside and vice versa passes through the firewall. A firewall can be placed at the border between the local LAN and the public Internet. Large organizations may use firewalls with many levels of functionality, or they may distribute them across various departments, but at least one firewall is positioned at the point of transit to/from the Internet.
- Only authorized traffic, as specified by the local security policy, will be allowed to pass.
- The firewall itself is secure, meaning it is immune to intrusion. It is therefore essential that it be designed and configured correctly to prevent it from being compromised.
The main firewall manufacturers are Cisco and Check Point. A firewall can also be easily configured in Linux using iptables (free software, usually included in Linux).
Firewall Classification
We can distinguish three types of firewalls:
- packet filter;
- stateful filter;
- application gateway (or proxy server)
They are sorted by increasing functionality, where each category corresponds to a level that adds functionality compared to the previous one. Therefore, the application gateway has more functionality than all the others. However, with the increase in functionality comes a greater an increase in configuration complexity.
